Alwaght- A 22-year-old cyber-security analyst accidentally halted the global spread of the NSA-Developed Ransomware, WannaCry, by buying a domain name hidden in the malware.
Spy tools developed by the US National Security Agency (NSA) have infected tens of thousands of computers in nearly 100 countries
The analyst, who tweets as MalwareTech and works for Kryptos Logic, a security firm, admitted he had not realized that buying the domain name, for just $10.69, would have this fortunate effect.
The domain name is believed to have been written into the software by the hackers to act as a kill switch.
Each time the program tried to infect a computer; it would try to contact the webpage. If it failed, WannaCry would carry on with the attack, but if it succeeded it would stop.
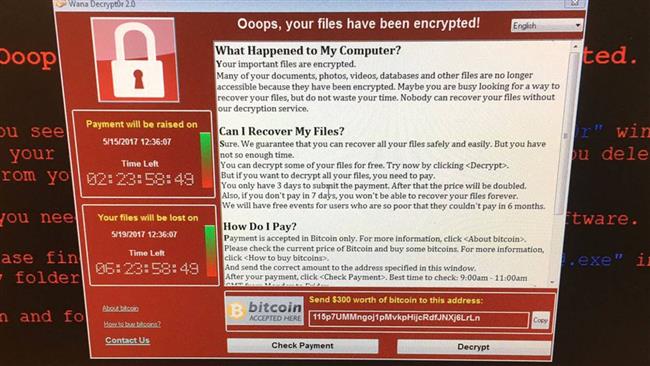
WannaCry has infected tens of thousands of computers across the world, shutting down vital systems used by the NHS in Britain.
The malicious malware locks down all the files on an infected computer and asks the administrator to pay $300 to $600 in order to restore access.
Researchers with security software maker Avast said they had tracked 75,000 cases of ransomware infections in 99 countries, with Russia, Ukraine and Taiwan being the top targets.
Speaking to the Daily Beast, MalwareTech said he noticed the domain name, a string of nonsensical letters ending in gwea.com, in the code.
|I saw it wasn’t registered and thought, ‘I think I’ll have that,’” he told the website.
After buying the domain name, he pointed it to a ‘sinkhole’ server in the US, hoping simply to get more information about WannaCry.
"Immediately we saw five or six thousand connections a second,” MalwareTech said.
He said this appeared to have stopped large numbers of attacks, but confessed he had done this “completely by accident".
"I will confess that I was unaware registering the domain would stop the malware until after I registered it, so initially it was accidental."
He also warned people should still take precautions because the hackers could simply slightly alter the program to carry on making attacks.
"If we did stop it, there’s like a 100 per cent chance they’re going to fire up a new sample and start that one again,” he said.
"As long as people don’t patch, it’s just going to keep going."